

Our Services
Our penetration testing service is flexible and can be customized to suit the unique needs of your organization. Whether you're looking to conduct a one-time assessment or establish a continuous testing program, our team of experts will work with you to design a solution that meets your specific needs.
Don't wait for a cyber attack to happen, be proactive and take control of your organization's cyber defense with Rocheston Vines. Contact us today to learn more about how our penetration testing service and Vines vulnerability assessment software can help secure your digital assets.
Comprehensive Penetration Testing
Our Vines software will scan for a wide range of vulnerabilities, including known and unknown ones, as well as potential misconfigurations and misuses of systems. It also can simulate attacks and provides a deep understanding of the impact of potential exploits to your organization. With this knowledge, our team of experienced penetration testers will provide you with a detailed report that includes a prioritized list of recommendations on how to secure your digital assets.
What is Penetration Testing?
Penetration testing can be performed manually or with the use of automated tools. It can be done by an organization's internal security team, or it can be outsourced to a third-party security firm. The process typically includes gathering information about the target system, identifying potential vulnerabilities, attempting to exploit those vulnerabilities, and reporting on the success or failure of the attempts.
Penetration testing is an important part of maintaining the security of a system and is commonly used to help organizations meet compliance requirements.
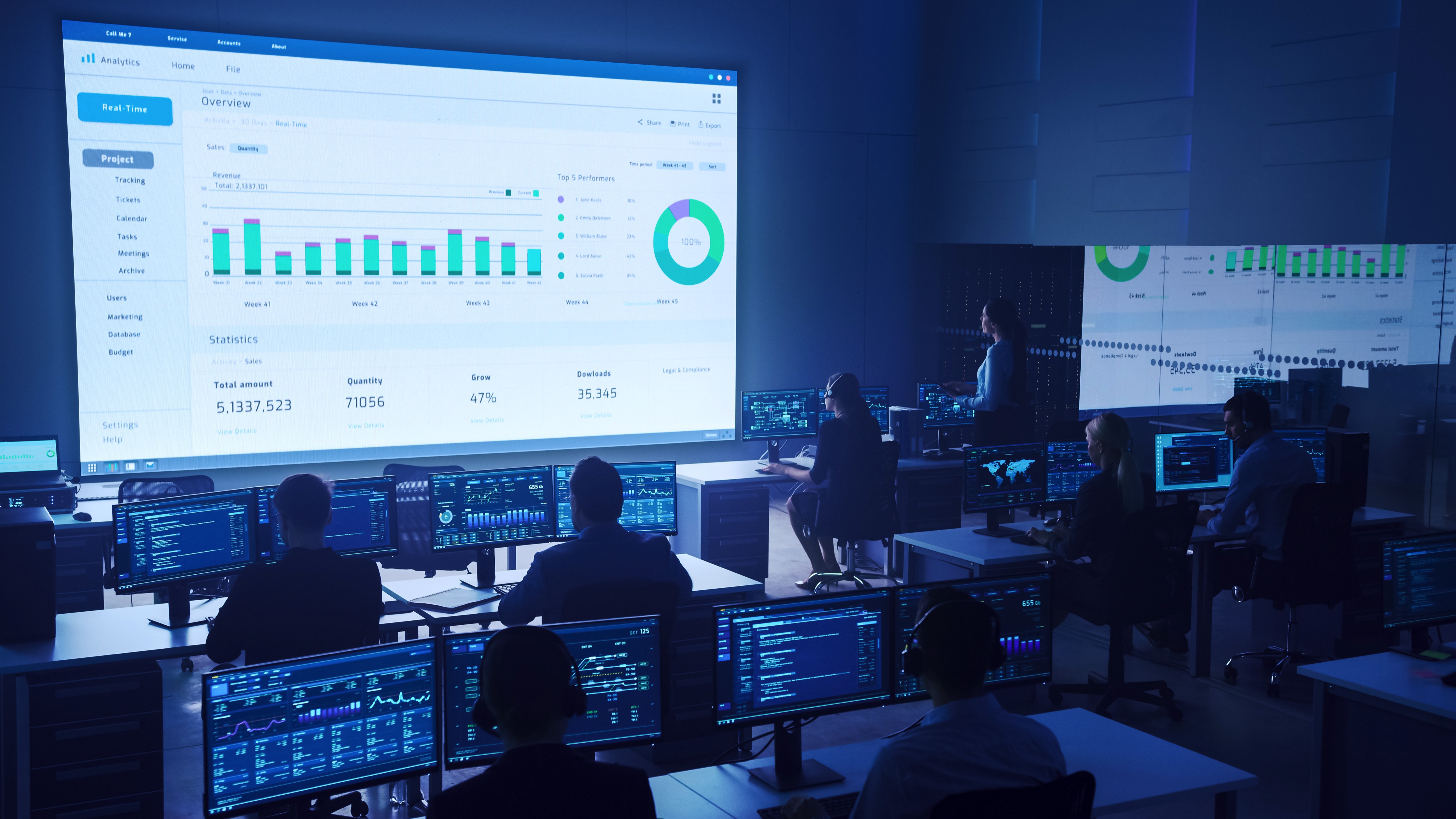
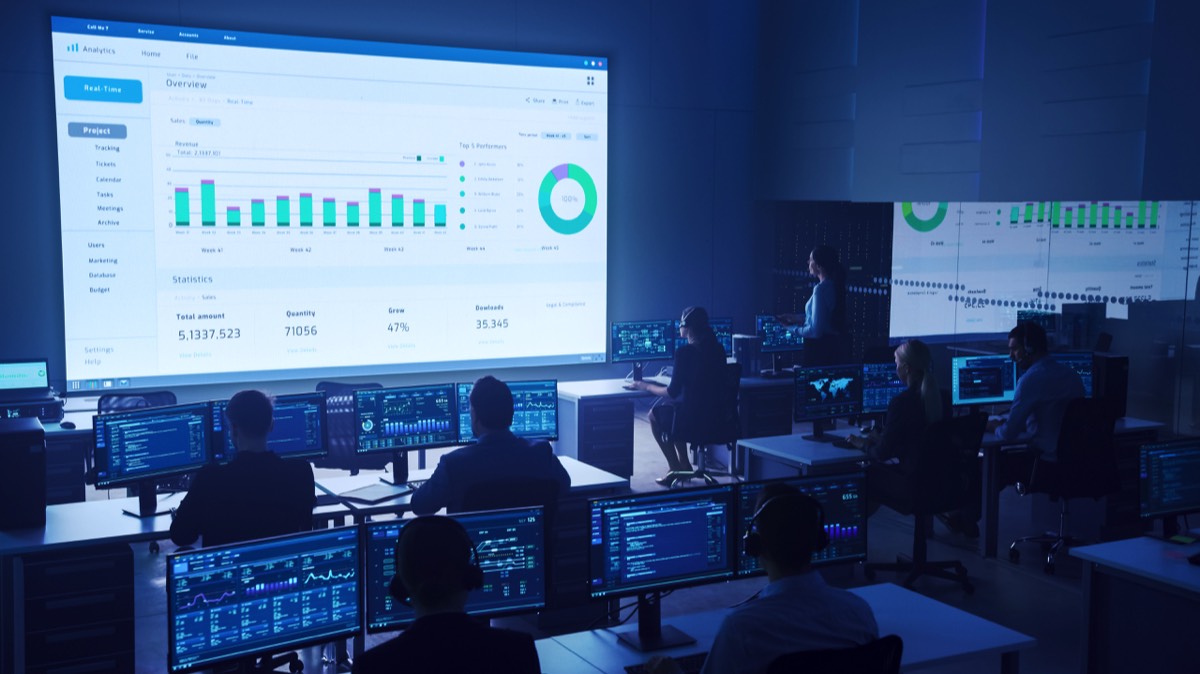
Detailed Report


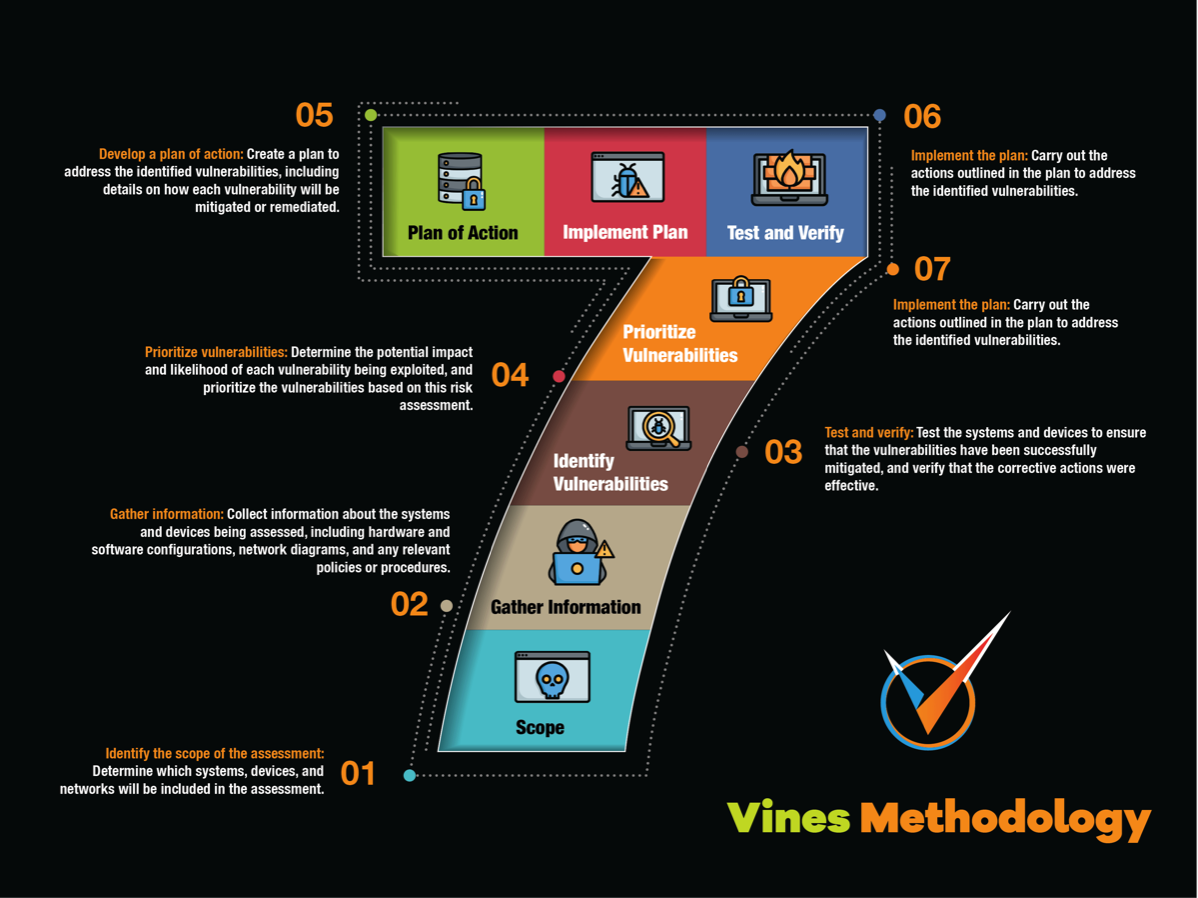
Our 7 Step Penetration Testing Methodology
- Identify the scope of the assessment: Determine which systems, devices, and networks will be included in the assessment.
- Gather information: Collect information about the systems and devices being assessed, including hardware and software configurations, network diagrams, and any relevant policies or procedures.
- Identify vulnerabilities: Use a variety of tools and techniques to identify vulnerabilities in the systems and devices being assessed.
- Prioritize vulnerabilities: Determine the potential impact and likelihood of each vulnerability being exploited, and prioritize the vulnerabilities based on this risk assessment.
- Develop a plan of action: Create a plan to address the identified vulnerabilities, including details on how each vulnerability will be mitigated or remediated.
- Implement the plan: Carry out the actions outlined in the plan to address the identified vulnerabilities.
- Test and verify: Test the systems and devices to ensure that the vulnerabilities have been successfully mitigated, and verify that the corrective actions were effective.
- To identify vulnerabilities: Penetration testing helps organizations identify weaknesses in their systems that could be exploited by hackers. By identifying these vulnerabilities, companies can take steps to fix them and improve their overall security posture.
- To protect assets and data: Hackers often target companies in order to steal sensitive data or disrupt business operations. By conducting penetration testing, companies can identify and address vulnerabilities that could be exploited by attackers, helping to protect their assets and data.
- To meet compliance requirements: Many industries have regulatory requirements that mandate the use of penetration testing as a way to ensure the security of systems and data. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires companies that handle credit card transactions to conduct regular penetration testing.
- To reduce the risk of a successful cyber attack: Conducting regular penetration testing can help organizations detect and fix vulnerabilities before they can be exploited by hackers. This can help to reduce the risk of a successful cyber attack and the resulting damage to a company's reputation and bottom line.


Penetration Testing Methodologies Used By Vine
- Black box testing: In black box testing, the tester has no knowledge of the internal workings of the system being tested. The tester only has access to the input and output of the system, and must use this information to identify vulnerabilities.
- White box testing: In white box testing, the tester has complete knowledge of the internal workings of the system being tested. The tester has access to source code, architecture diagrams, and other detailed information about the system.
- Gray box testing: Gray box testing is a combination of black box and white box testing. The tester has some knowledge of the internal workings of the system being tested, but not complete knowledge.
- External testing: External testing involves testing a system from the perspective of an outsider trying to gain access to the system over the internet.
- Internal testing: Internal testing involves testing a system from the perspective of an insider, such as an employee or contractor, who has legitimate access to the system.
- Targeted testing: Targeted testing involves focusing on a specific aspect or component of a system, such as a web application or network infrastructure.
- Blind testing: Blind testing involves testing a system without any prior knowledge of the system or its vulnerabilities. This is typically used to simulate the actions of a real-world attacker who has no inside knowledge of the system.
- Double-blind testing: Double-blind testing is similar to blind testing, but even the tester does not know the specific details of the system being tested. This is used to simulate the actions of a completely unknown and unpredictable attacker.


