








Our penetration testing services include:
- Network penetration testing: We'll test your network infrastructure and devices to identify vulnerabilities and evaluate your overall security posture.
- Web application penetration testing: We'll test your web-based applications, including web servers, databases, and custom code, to identify vulnerabilities and provide recommendations for remediation.
- Mobile application penetration testing: We'll test your mobile applications for vulnerabilities and provide recommendations for remediation.
- Social engineering: We'll test the human element of your security by attempting to obtain sensitive information through non-technical means.
Don't wait until it's too late – contact us today to learn more about our penetration testing services and take the first step in securing your business.
Penetration Testing

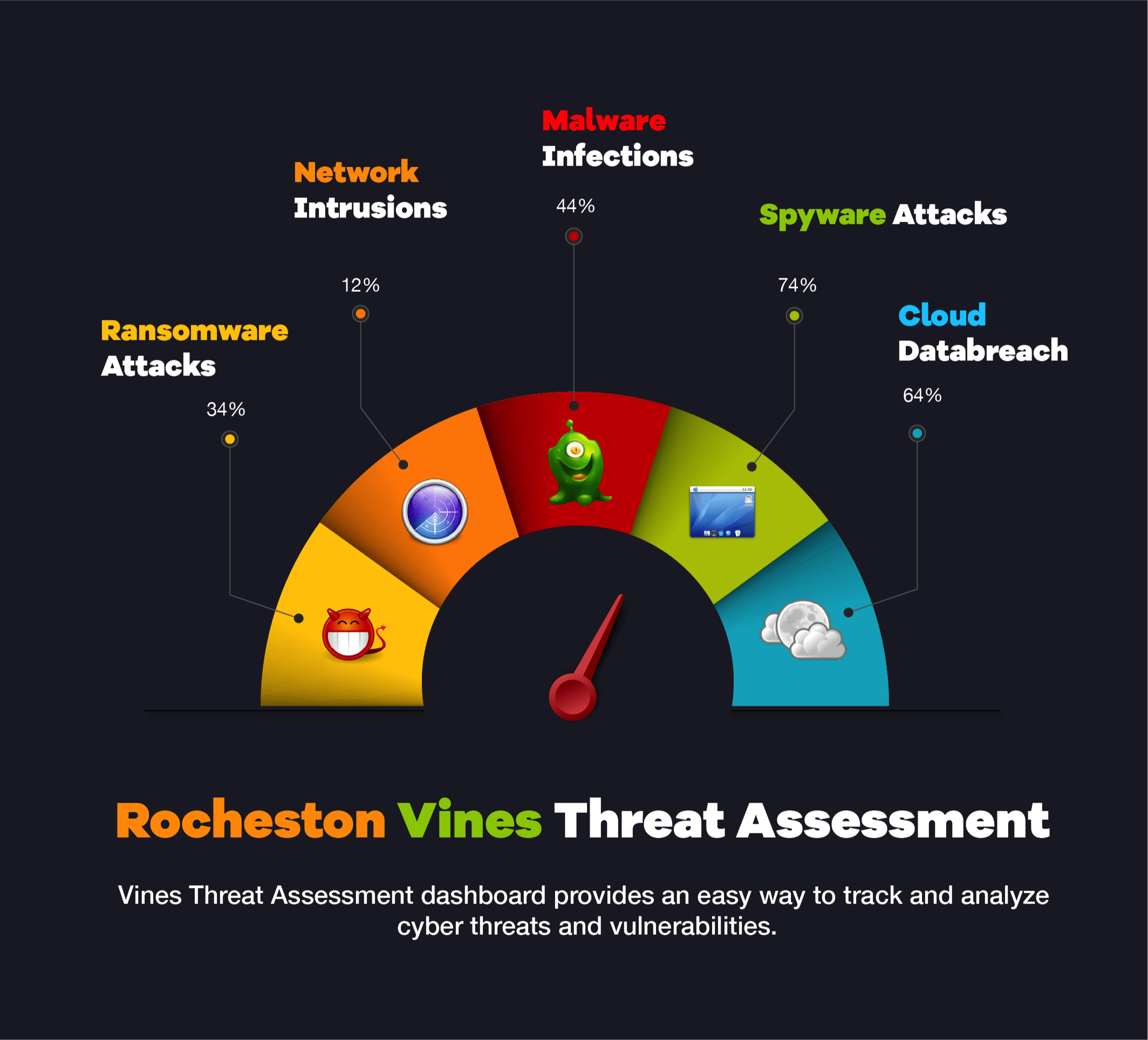
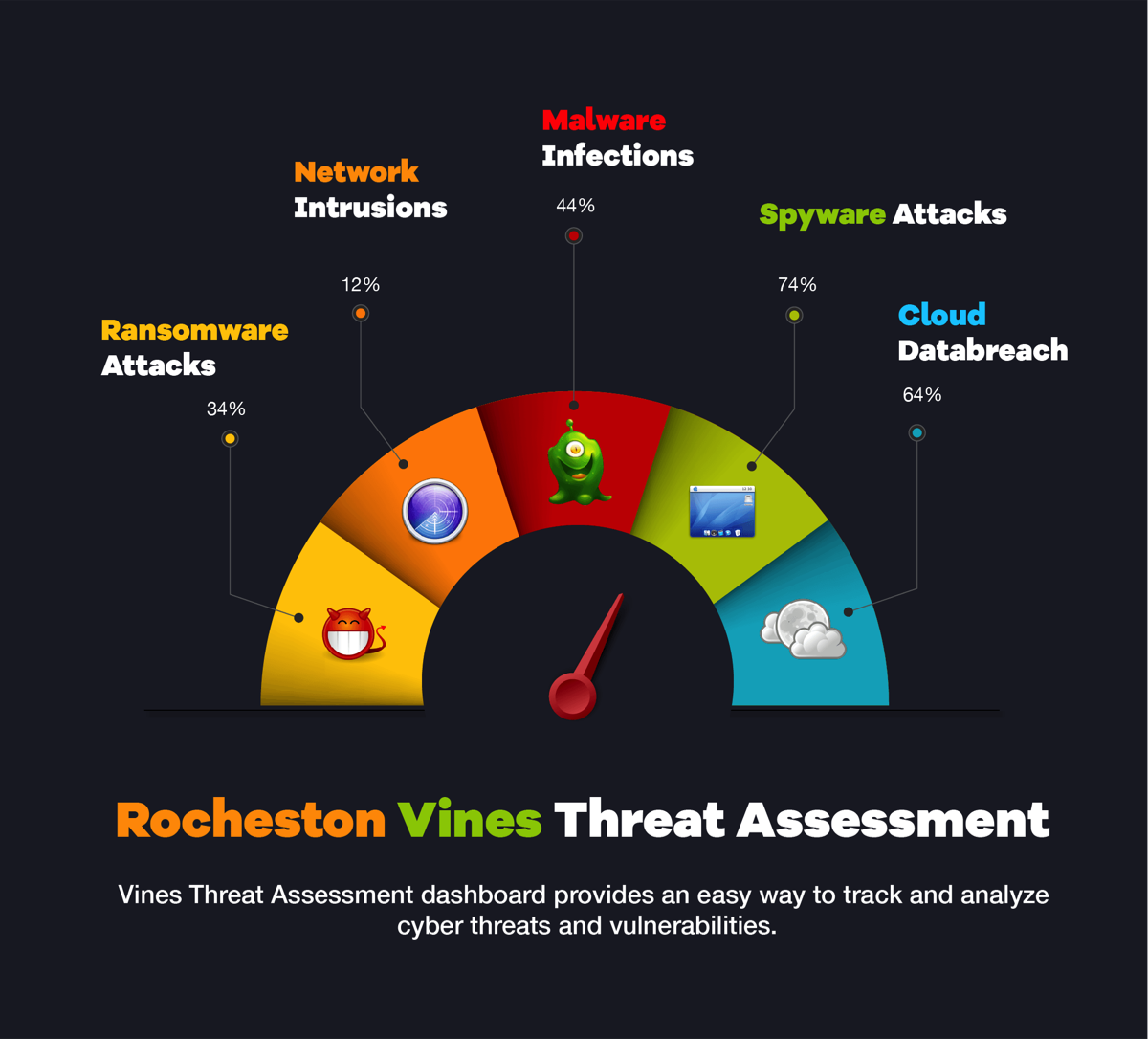

Audits and Assessments
Threat Intelligence


Incident Response
Vulnerability Vines


Databreaches
RCCE Certification



